Flirting with Fraud: Why Sextortion Is the Most Devastating Dating Scam
13.2.2025 14:00:00 CET | Business Wire | Press release
Sextortion has emerged as one of the most dangerous forms of romance scams, preying on online daters and, tragically, claiming the lives of teenagers. Fraudsters use fake profiles to lure victims into sharing intimate content, only to threaten exposure unless a ransom is paid. Regula, a global developer of identity verification (IDV) solutions, shares a vision of how social media and dating platforms can strengthen protections to safeguard users.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20250213790016/en/

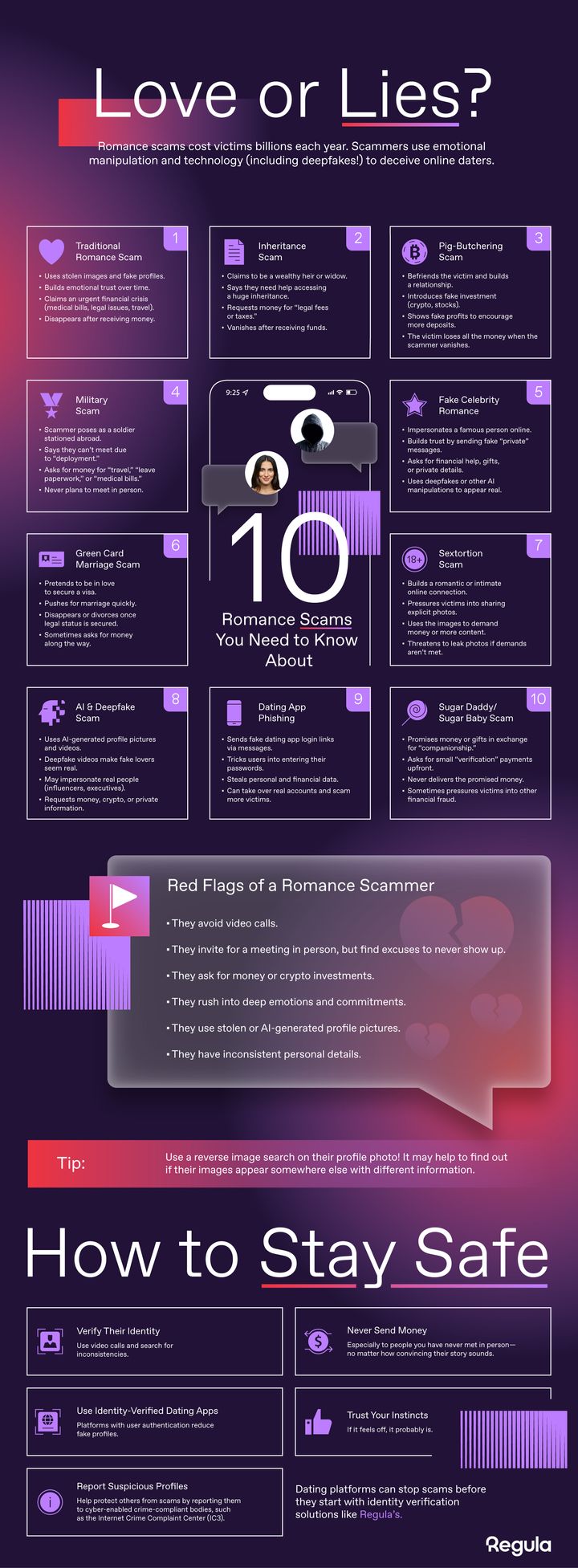
Can you spot a romance scam? Scammers are getting smarter, using fake identities, AI, and emotional manipulation to exploit trust. See how these scams work and what can be done to stop them. (Graphic: Regula)
Romance scams come in many forms, exploiting trust and emotional vulnerability to defraud victims. Their common tactics include:
- Catfishing: Scammers create fake identities to build trust and manipulate victims.
- Military Scams: Fraudsters pose as deployed soldiers seeking financial assistance.
- Inheritance Scams: Victims are deceived with false claims of large inheritances requiring upfront fees.
- Pig-Butchering (Crypto Investment) Scams: Scammers feign romantic interest to lure victims into fraudulent investment schemes.
However, according to reports from leading child safety organizations, including the National Center for Missing and Exploited Children (NCMEC) and Thorn, sextortion is one of the most severe threats, with cases surging at an alarming rate. The FBI reported over 12,000 complaints in 2023 alone, resulting in millions in financial losses, severe psychological trauma, and, in some cases, even fatalities. Younger users and those new to online dating are particularly vulnerable.
Common sextortion tactics include:
- Fake Identities: Scammers pose as attractive singles, influencers, or even celebrities to build quick trust.
- Rapid Escalation: Conversations quickly shift from introductions to intimate exchanges.
- Blackmail Threats: Once explicit content is shared, scammers demand money, cryptocurrency, or further compromising images under the threat of exposure.
- AI-Driven Deception: Some scams leverage deepfake videos or AI-powered chatbots to manipulate victims.
The Role of Identity Verification in Preventing Sextortion
Sextortion thrives in environments where fake profiles and anonymity enable bad actors to operate freely. Social media and dating platforms play a critical role in combating this threat—through proactive moderation, AI-powered content monitoring, and user education. Stronger identity verification during registration is also a valuable tool in this arsenal, but it must be implemented thoughtfully, balancing fraud prevention with user privacy and accessibility.
Different online platforms use varying levels of verification, ranging from strongest to weakest:
- ID & Biometric Verification – Matching government-issued IDs with real-time selfies for authentication.
- Real-Time Selfies Without ID Validation – Confirming a live presence but without a verified identity document.
- Basic Checks – Verification through phone numbers, email, or linked social media accounts.
- Self-Reported Identity Without Validation – The least secure method, relying solely on user-provided information.
How Biometric and ID Verification Strengthens Security:
- Eliminating Fake Profiles: Biometric checks make it significantly harder for scammers to create fake accounts.
- Anti-Spoofing Technology: Prevents impersonation by detecting fraudulent attempts using photos or masks.
- Liveness Detection: Confirms a real person is present, preventing AI-generated deception.
“When faced with strong verification measures, scammers don’t simply disappear—they move to less secure platforms where they can continue their schemes unchecked. Standardizing biometric ID verification across multiple platforms would make it significantly harder for them to do so, creating a safer ecosystem across social media, dating apps, and other online services." – Jan Stepnov, Identity Verification Expert at Regula.
Empowering Users to Stay Safe
While platforms must take stronger security measures, users can also protect themselves by:
- Being Cautious of Fast-Moving Relationships: Avoid engaging in intimate exchanges early in conversations.
- Interacting with Verified Users: Prioritize connections with verified profiles.
- Reporting Suspicious Activity: Flagging blackmail attempts and scam behavior.
- Never Paying Ransoms: Complying with extortion often leads to further threats.
For more insights on how identity verification is transforming online dating security, visit Regula’s blog.
About Regula
Regula is a global developer of forensic devices and identity verification solutions. With our 30+ years of experience in forensic research and the most comprehensive library of document templates in the world, we create breakthrough technologies for document and biometric verification. Our hardware and software solutions allow over 1,000 organizations and 80 border control authorities globally to provide top-notch client service without compromising safety, security, or speed. Regula has been repeatedly named a Representative Vendor in the Gartner® Market Guide for Identity Verification.
Learn more at www.regulaforensics.com.
View source version on businesswire.com: https://www.businesswire.com/news/home/20250213790016/en/
Subscribe to releases from Business Wire
Subscribe to all the latest releases from Business Wire by registering your e-mail address below. You can unsubscribe at any time.
Latest releases from Business Wire
AI Meets Traditional Culture: Huangshan Captures Widespread Attention at ITB Berlin7.3.2026 10:22:00 CET | Press release
Huangshan, one of China’s most iconic scenic destinations, drew significant attention at this year’s ITB by presenting a compelling fusion of traditional Chinese culture and cutting-edge artificial intelligence under the slogan “The world of Huangshan is for the world.” This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20260307909978/en/ International visitor admires Huangshan cultural and creative exhibits at the Huangshan stand during ITB Berlin. Located in eastern China’s Anhui Province, Huangshan is famed for its “Five Natural Wonders” — fantastic pines, grotesque rocks, sea of clouds, hot spring and winter snow. The mountain is widely regarded as one of China’s greatest mountain landscapes. It is also a rare natural heritage site that simultaneously holds multiple international designations, including UNESCO World Cultural and Natural Heritage status, a UNESCO Global Geopark and a World Biosphere Reserve. At ITB, the Huangsh
Incyte Announces the European Commission Approval of Zynyz® (retifanlimab) for the First-Line Treatment of Advanced Squamous Cell Carcinoma of the Anal Canal (SCAC)6.3.2026 22:42:00 CET | Press release
- Zynyz® (retifanlimab) in combination with carboplatin and paclitaxel (platinum-based chemotherapy) is the first systemic treatment for adult patients with advanced SCAC in Europe- The EC approval is based on results of the POD1UM-303 study which showed that adult patients with advanced SCAC achieved significantly improved progression-free survival with Zynyz in combination with carboplatin and paclitaxel as a first-line treatment compared to chemotherapy alone.1 Incyte (Nasdaq:INCY) today announced that the European Commission (EC) has approved Zynyz® (retifanlimab) in combination with carboplatin and paclitaxel (platinum-based chemotherapy) for the first-line treatment of adult patients with metastatic or with inoperable locally recurrent squamous cell carcinoma of the anal canal (SCAC). “The EC approval of Zynyz marks an important step forward for patients with advanced SCAC, a rare cancer for which meaningful treatment advances have not occurred in several decades,” said Bill Meur
Dfns Launches Payouts6.3.2026 21:27:00 CET | Press release
Dfns today announced the launch of Payouts, a new API enabling institutions to convert stablecoins to fiat and route payouts across multiple bank accounts while keeping wallet-level governance and controls in place. This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20260305327930/en/ Convert stablecoins to fiat and settle payouts to bank accounts in 94 countries, today. Solving the problem of single-rail off-ramps Today, most fintechs and institutions still hard-wire a single payout provider into their stack, or rely on vertically integrated models that bundle routing, pricing, custody, and settlement together. That approach may be convenient early on, but it creates structural problems at scale: weak price discovery because there is no competitive pressure on margins, limited auditability because routing decisions are opaque, and operational fragility because a single provider degradation in any corridor requires architectural i
Klarna Group Plc Clarifies Mechanics of March 9 Lock-Up Expiration6.3.2026 20:23:00 CET | Press release
Klarna Group plc (NYSE: KLAR) today issues the following clarification to ensure investors and market participants have accurate information regarding the mechanics of its lock-up expiration on March 9, 2026, the processes required before pre-IPO shares can be traded on the NYSE, and the prior liquidity opportunities already available to shareholders. This release contains only factual descriptions of the Company's share structure and applicable processes. It does not constitute guidance or a projection of any kind regarding future trading volumes, share price, or the intentions of any shareholder and speaks only as of the date of this press release. 1. 335 million locked-up shares — but two different categories Of the 378 million total ordinary shares outstanding, approximately 335 million are subject to lock-up restrictions expiring March 9, 2026. However, these shares fall into two distinct categories governed by separate sets of regulations. A. 159 million shares (48% of locked-up
Lone Star Funds Announces Agreement to Acquire the Capsules & Health Ingredients Division of Lonza Group AG6.3.2026 18:30:00 CET | Press release
Lone Star Funds (“Lone Star”) today announced that an affiliate of Lone Star Fund XII, L.P. has entered into a definitive agreement to acquire the Capsules & Health Ingredients (“CHI”) division of Lonza Group AG. As part of the transaction, Lonza will retain a 40% equity position in the business. Headquartered in Basel, Switzerland, CHI operates globally across the Americas, Europe and Asia Pacific. The business comprises three segments: Hard Empty Capsules: leading global manufacturer of gelatin and plant-based capsules offering a broad range of innovative solutions for pharmaceutical and nutraceutical customers. Dosage Form Solutions: end-to-end development and manufacturing platform serving nutraceutical and pharmaceutical customers. Health Ingredients: provider of branded, science-backed nutrition ingredients serving joint health, energy and active lifestyle markets. Lone Star believes CHI is a high-quality, globally recognized platform with strong technical capabilities, different
In our pressroom you can read all our latest releases, find our press contacts, images, documents and other relevant information about us.
Visit our pressroom